Embrace Cybersecurity Awareness Month: 3 Quick & Easy Security Wins!

It’s October, which means it’s not only the spookiest time of the year, but also CyberSecurity Awareness month! To give you a sense of the current cybersecurity landscape, there are 2,200 cyber attacks per day, with a cyber attack happening every 39 seconds on average.
Cybersecurity isn’t just an IT responsibility. Your entire staff can play a part in safeguarding company and personal data — here are 3 Quick & Easy Security Wins that you can be doing today (your IT teams will thank you!)
"Security is always excessive until it's not enough."
- Robbie Sinclair, Head of Security, Country Energy, NSW Australia
CyberSecurity: Whether you’re at this stage or not, keeping ourselves secure on the internet, especially in this age, should be as commonplace as locks on the doors to our home, numeric pins on our debit cards, or biometric scanners on our modern smartphones.
We protect these assets because we deem them valuable, but why not our digital assets or identities?
A few helpful statistics that shed some light on the current landscape:
- The United States remains the most highly targeted country with 46% of global cyberattacks being directed towards Americans. (Watters)
- 71.1 million people fall victim to cyber crimes yearly. (PurpleSec)
- Individuals lose $4,476 USD on average. (PurpleSec)
- Fraud cases are up 70% since 2020. (Watters)
- Phishing attacks increased by 48% in the first half of 2022. (Watters)
- Ransomware is 57x more destructive in 2021 than it was in 2015. (PurpleSec)
The Internet of Things (IoT) is only going to continue to proliferate as time goes on. As it does, so too will the threats. But just know, everyone can play a part in safeguarding company and personal data — and here are 3 Quick & Easy Security Wins that you can be doing today.
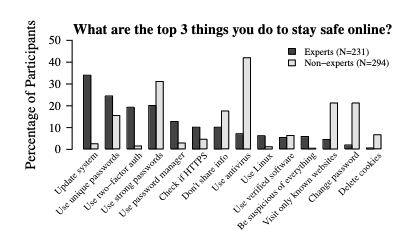
Percentage of participants zero to fifty for various methods of staying safe.
Left to right: Update system, use unique passwords, use two-factor authentication, use strong passwords, use password manager, check if HTTPS, don't share info, use antivirus, use linux, use verified software, be suspicious of everything, visit only known websites, change password, delete cookies.
Expert and non-experts do not rank items the same.
Experts chose update system as number one and non-experts chose use antivirus.
According to a publication titled “‘...no one can hack my mind’: Comparing Expert and Non-Expert Security Practices” for the Eleventh Symposium On Usable Privacy and Security, experts agreed that the top three things you can do to stay safe online are to:
- Update systems
- Use unique passwords
- Use two-factor authentication
Contradictory to this, the majority of the surveyed non-experts thought that “using antivirus”, “using strong passwords”, and “visiting only known websites” and “changing passwords” are the top three methods to stay safe (last two are tied for third). The disparity here is telling, as it paints a picture of out-of-touch public that is emphasizing their security efforts on the wrong avenues. Guess what? It’s time to fix this.
1. Update Your Systems
Do not swipe that notification to update your phone, laptop, or desktop. System OS and software updates may seem innocuous, but they will typically contain important patches or fixes that “close the door” on vulnerabilities. By updating your systems to the latest version, amongst other benefits, you are fortifying your device against the latest threats and vulnerabilities that an attacker might try to exploit.
2. Use Unique Passwords
While a strong password is good, it can be [applied] better. Enter the unique password. Simply put, a unique password is a strong password unique to a singular application. A unique password minimizes your vulnerability across your other identities in the event where the password has been compromised. Since it’s unique to one application, and contains no reiterable data, it will not be possible for an attacker to use this password across other applications.
3. Multi-factor Authentication (also known as two-factor authentication)
An incredibly easy and quick way to increase the security of your digital identities is to avail Multi-factor Authentication (MFA) where available. MFA can take many forms, with varying degrees of security (a bit on this later), but the general principle is the same across; MFA provides an additional layer of security, where a user will need to verify that they are the individual associated with the account, typically by sending an one-time passcode (OTP).
MFA does not need to be enabled on every single account, but, at a minimum, it should be enabled on critical identities, such as those associated with banking, healthcare, utilities, and other essential services - anything that is critical to your livelihood, and holds sensitive data.
Not all MFA are created equal though. MFA methods that send OTP codes via SMS or email are the weakest of the bunch, as these methods are the most susceptible to phishing, social engineering, or on-path (also known as man-in-the-middle [MiiM]) attacks. Generally speaking, the more secure methods are in the following order: authenticator tokens (i.e., software-based token generators, physical token fob), biometrics, and hardware keys (i.e.,YubiKeys, FIDOKeys). For optimal results, utilize multiple secure methods simultaneously.
Can’t Remember Your Passwords? Great, Use a Password Manager!
Password Managers are a competent means to hold all our invaluable passwords, securely behind a fortified, singular point-of-entry: akin to a bank vault. Since gaining prominence within the past decade, they’ve effectively altered the way in which we think and secure our passwords. So much so, that “four times more experts than non-experts said that using a password manager is one of the most important things they do to stay safe online” (Lon et al.).
Out of the many benefits of Password Managers is the incredible ease of creating and utilizing strong, unique passwords. You no longer need to use “password123” for all your accounts, or try to remember, or create, strong passwords for all of your accounts.
Modern managers even offer: methods to securely share passwords, team/family integrations, creating/associating MFA passwords, scanning services to access your saved credentials, and even storing some basic files.
Lastly, it should be noted that simply using a Password Manager does not mean you're secure. A poorly protected Password Manager would essentially be like leaving the key to your house under your doormat. If you’re going to use a password manager, protect it with secure MFA methods.
Password Hygiene
Passwords should follow simple rules:
- Be no less than 16 characters. The more characters, the stronger the password, but 16 is a good compromise.
- Incorporate special characters, numbers, and uppercase and lowercase letters
- Do NOT include any personal identifying information in the password
- Be unique to each site
- Optimally: Be completely random
If #5 is a step too far, you can still generate a unique, strong password that is memorable, such as: “flossy.respond5maroon4GRAIL0crutch*teacher” (do not use this as a password, since this is now public information). Perhaps not as memorable as your Mother’s maiden name, it can be achieved, and satisfies all of the above rules and requirements.
TIP: Usernames are also common attack vectors, because they are typically half of a user’s login. While usernames need not follow those same, strict rules as above, it is good practice to keep them unique to each site.
At Sandstorm, we take security very seriously, it’s an integral part of everything we do. For example, when major security events occur, like Drupalgeddon 2.0; our security team is able to assess the situation quickly and spring into action. In this case of Drupalgeddon 2.0, our teams applied security updates to more than 30 sites in a single afternoon.
In addition, Sandstorm has an established and documented Security Policy, in addition to processes for information security, privacy, and the use of tools like MFA to safeguard data.
That being said, having a more proactive strategy for cybersecurity and security protocols (both organizationally and personally) is critical to success. Connect with our security team today to discuss security strategies, policies and processes; we’d love to help!
Works Cited
Lon, Lulia, et al. Proceedings of the Eleventh Symposium On Usable Privacy and Security. 2015. Google,
PurpleSec. “Cyber Security Statistics The Ultimate List Of Stats Data, & Trends For 2023.” Managed Cyber Security Services | PurpleSec (Becoming SecureTrust Cyber), 2023. Accessed 10 October 2023.
Watters, Ashley. “Top 50 Cybersecurity Statistics, Figures and Facts.” CompTIA, 2023. Accessed 10 October 2023.



